Why is the shellshock such a big deal?
Shellshock is a vulnerability in the bash shell. This vulnerability has been lying unnoticed for more than 20 years.
Bash – the shell of choice for almost everyone
Bash shell is arguably the most common shell for Unix and Unix based operating systems. This is where every command takes place, including commands that applications run behind the scenes. Unix is extremely prevalent,it runs almost everything from smart phones, to web servers and almost everything in between. The problem is, this shellshock vulnerability is so easy to use, that I wouldn’t be surprised if thousands of web servers, have already been compromised.
This bug was recently discovered, but it has been laying unnoticed for more than 20 years. That’s right, bash has had this bug since shortly after it was created in 1989. That’s a long time for a bug to lay dormant. I’m sure someone has discovered this already, but only in 2014 are we officially hearing this. This means, many systems have probably already been compromised long before today. The implications of this bug are massive.
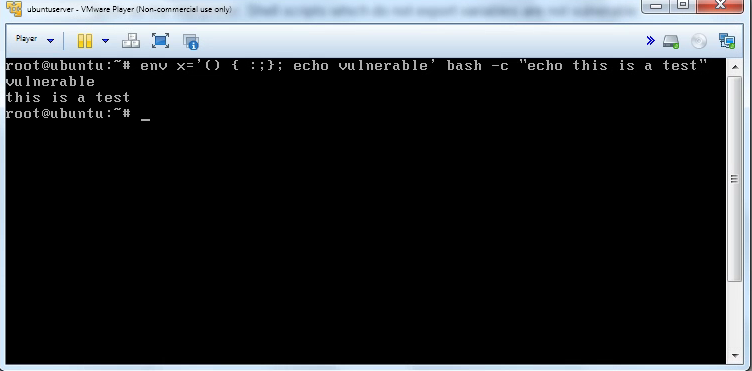
The below can be run to tell you if you are vulnerable to the shellshock bug.
$ env var='() { :;}; echo vulnerable' bash -c "echo this is a test"
What is happening here is you are setting an environment variable. These are great ways to save time. Unfortunately “() { :;}; ” causes whatever is following it to be run as a literal command rather than a text string. In the above example, it’s just echoing the word vulnerable. But that command could be literally anything, and could give a malicious user full control over the system.
Web servers aren’t the only systems left vulnerable to the shellshock bug. This also affects Mac OS X and almost any Linux desktop.
In theory if someone were to craft a specially designed DCHP packet, any system running an unpatched bash shell could be fully compromised. DHCP is the protocol almost every computer uses to get an IP address. If you’re connected to the internet, you have an IP, if you have an IP you probably got it through DHCP. This needs to be taken seriously. While DHCP attacks aren’t extremely likely, web servers, specifically those running CGI are the most vulnerable to this bug as that’s the easiest attack vector to automate.
The good news
The good news is there’s already patches being released by vendors. Which means, if you’re on a Unix system all you have to do is upgrade to the latest version in the repository. Unfortunately, it would appear that at the time of this writing Mac users are still left vulnerable to the Shellshock bug.

Recent Comments